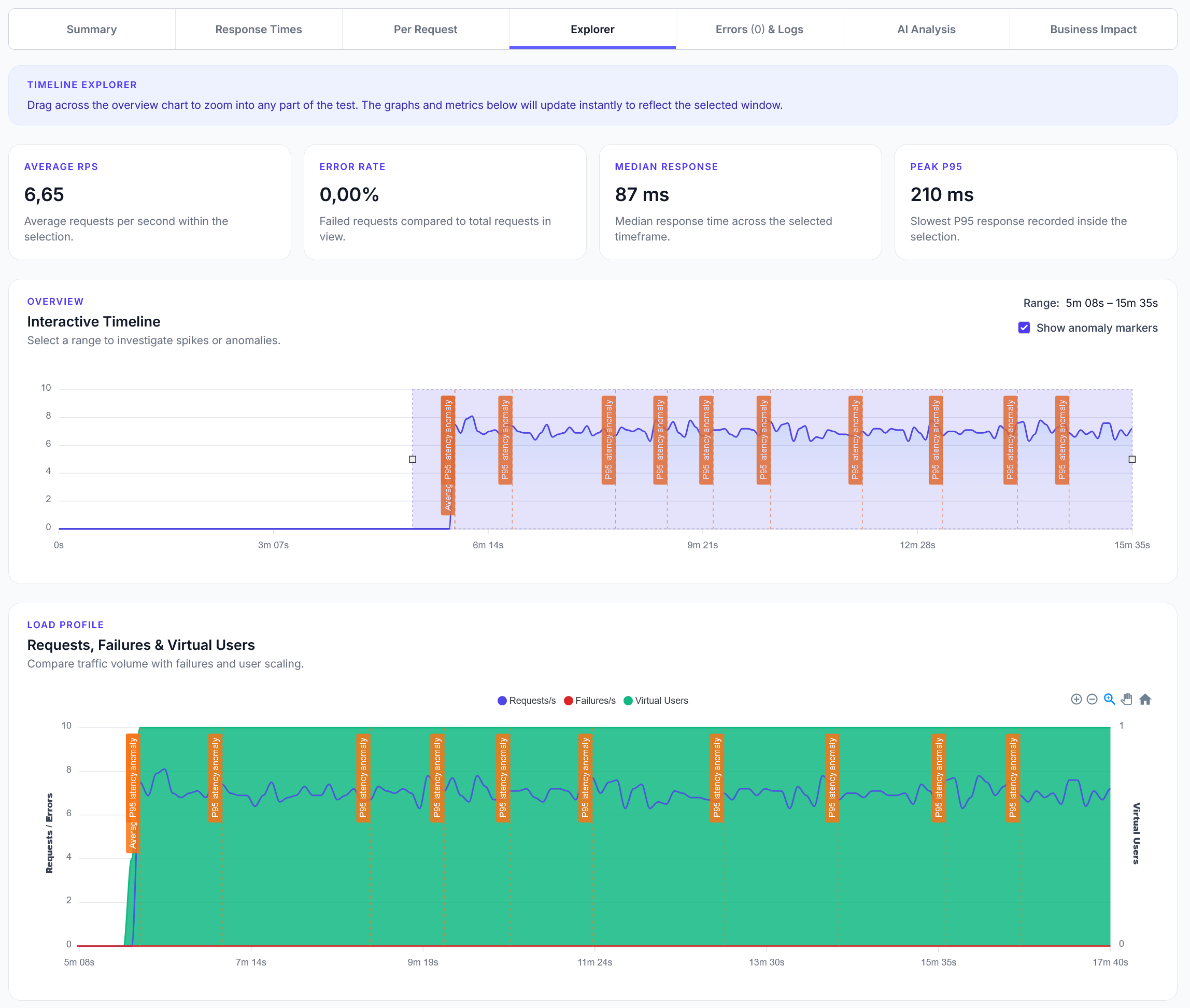
Explorer reports addition
We have added a new Explorer feature to reports, with a timeline scrubber and easy anomaly detection.
TLDR: Automated security headers testing with tools like LoadForge enables QA teams to efficiently discover and validate security headers across websites, offering configurable settings and detailed reporting to prevent vulnerabilities such as XSS and clickjacking without manual oversight. This approach ensures consistent security via continuous monitoring, integration with CI/CD, and targeted alerts for configuration issues, ultimately protecting users from potential attacks.
Security header misconfigurations aren't just technical oversights—they create real vulnerabilities that expose your users to XSS attacks, clickjacking, and data breaches. But manually checking security headers across every page? That's time-consuming and error-prone at scale.
Instead of manually auditing headers page by page, modern QA teams use automated crawlers that systematically discover and validate security headers across your entire website. Here's how it works:
Intelligent Site Discovery
Comprehensive Security Headers Validation
The best part? You can easily configure which headers are required for your security posture:
REQUIRED_HEADERS = {
'Strict-Transport-Security': True, # HSTS - highly recommended
'X-Frame-Options': True, # Clickjacking protection
'X-Content-Type-Options': True, # MIME type sniffing protection
'Referrer-Policy': True, # Referrer information control
'Content-Security-Policy': False, # CSP - optional by default
}
Simple Configuration Options:
Choose the validation depth that matches your security requirements:
Simple Security Headers Crawler
Comprehensive Security Validation
Run these security validations automatically to maintain protection:
When security header issues are detected, you'll know immediately through:
This proactive approach means you can fix security gaps before they're exploited by attackers.
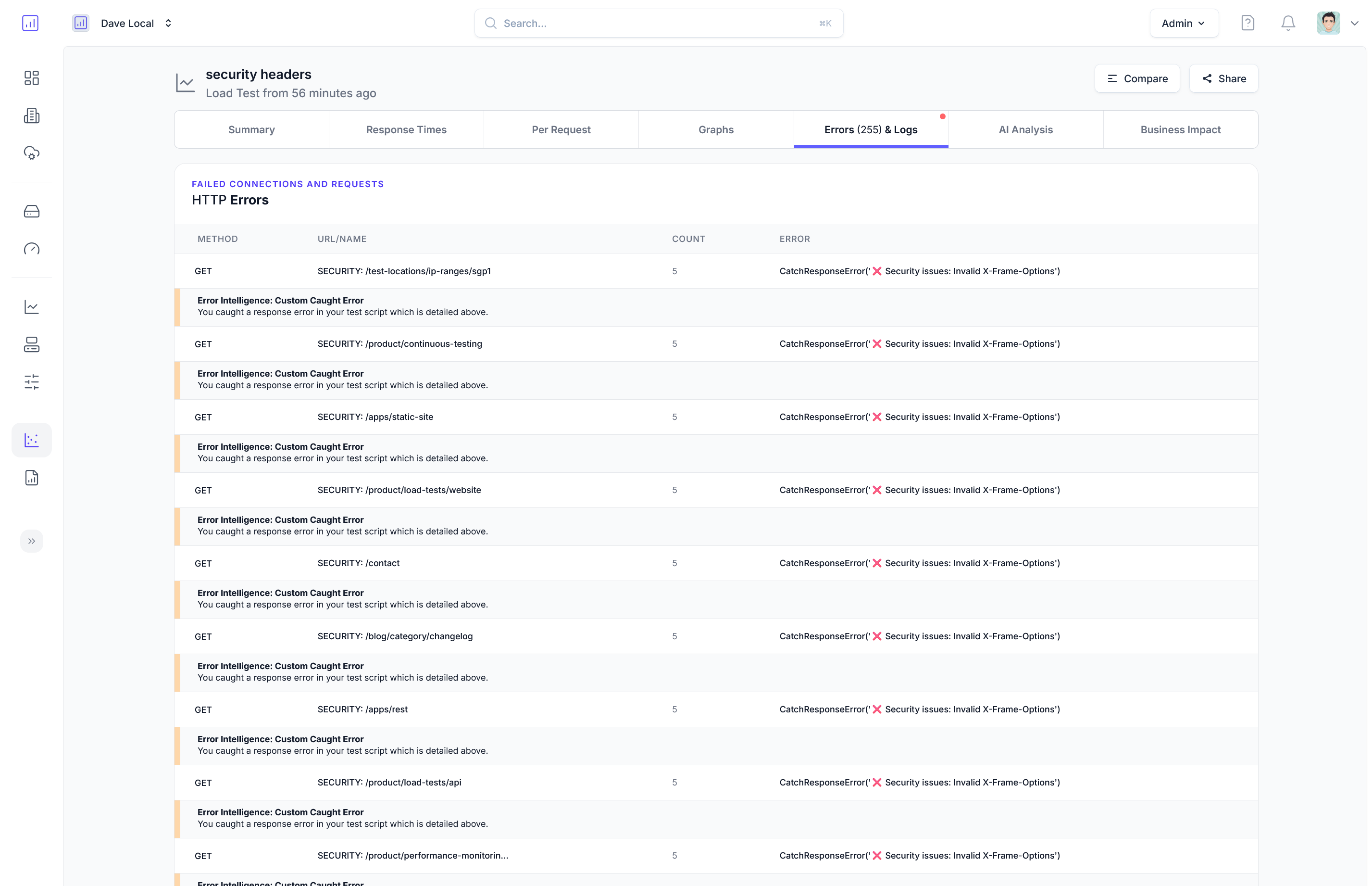
LoadForge automatically passes/fails tests for you, but this script also provides detailed security reporting:
[from worker loadforge-684fb9541238f9] Starting security headers validation...
[from worker loadforge-684fb9541238f9] Required headers: ['Strict-Transport-Security', 'X-Frame-Options', 'X-Content-Type-Options', 'Referrer-Policy']
[from worker loadforge-684fb9541238f9] SECURITY ISSUE [HIGH]: Missing required header: X-Frame-Options on /login
[from worker loadforge-684fb9541238f9] SECURITY ISSUE [HIGH]: Missing required header: Strict-Transport-Security on /api/users
[from worker loadforge-684fb9541238f9] SECURITY ISSUE [MEDIUM]: Invalid X-Content-Type-Options: text/html on /admin
[from worker loadforge-684fb9541238f9] SECURITY HEADERS STATUS: 12 total issues (8 high, 4 medium) across 47 pages
Manual security header audits are inconsistent and can't keep up with deployment frequency. Automated testing:
The comprehensive version automatically classifies pages and applies appropriate security requirements:
LoadForge will automatically flag bad URLs as failing, but also logs debug info as shown below:
[from worker loadforge-684fc7e32bcec4_2412bf02c8414657931f88cf4d1a2dbb] Starting security headers validation...
[from worker loadforge-684fc7e32bcec4_2412bf02c8414657931f88cf4d1a2dbb] Required headers: ['Strict-Transport-Security', 'X-Frame-Options', 'X-Content-Type-Options', 'Referrer-Policy']
[from worker loadforge-684fc7e32bcec4_2412bf02c8414657931f88cf4d1a2dbb] SECURITY ISSUE [MEDIUM]: Invalid X-Frame-Options: sameorigin on /pricing
[from worker loadforge-684fc7e32bcec4_2412bf02c8414657931f88cf4d1a2dbb] SECURITY ISSUE [MEDIUM]: Invalid X-Frame-Options: sameorigin on /apps/static-site
[from worker loadforge-684fc7e32bcec4_84c630ef916e4cbfab305883efd8f10e] SECURITY ISSUE [MEDIUM]: Invalid X-Frame-Options: sameorigin on /
[from worker loadforge-684fc7e32bcec4_84c630ef916e4cbfab305883efd8f10e] SECURITY ISSUE [MEDIUM]: Invalid X-Frame-Options: sameorigin on /pricing
Setting up automated security headers testing is straightforward. We've created LoadForge scripts at two complexity levels to match your security maturity.
Get the complete security headers validation scripts →
Choose your level:
Don't let missing security headers expose your users to attacks. Automate the validation, maintain consistent security standards, and protect every page without the manual overhead.
LoadForge Team
The LoadForge Team